This section will introduce some advanced techniques for using private services.
This is a multi-page, printable view of this section. Click here to print.
Advanced Features
- 1: Blocked Applications List
- 2: Enhancing CDN Access Speed with ECS
- 3: DDNS Dynamic Resolution
- 4: DNS Split Configuration Guide
- 5: Using Custom Device Names
- 6: Faster Request Response
- 7: Setting Up Trusted Service Providers
1 - Blocked Applications List
It is important to avoid confusion: blacklists are typically used to block ads, privacy intrusions, malware, etc., while the Blocked Applications List is used to completely block the use of specified applications.
This is often used in conjunction with a schedule for personal habit formation to prevent addiction. It is commonly used for habit formation in minors, for example: prohibiting the use of social media and games during study time. It can also be used for self-discipline in adults, for example: prohibiting the use of social media and games during work hours.
This service pre-configures some rules based on popular applications in various countries. Due to changes in popular culture and business developments, these lists may become outdated, but we are committed to ongoing maintenance.
If you find that an application on the list is not fully blocked, or if you need to add a recently popular application, please contact us, and we will address it promptly.
Need Help
Contact WeChat
adguard6688
Or
Send Email
service1@adguardprivate.com
Please describe the issue you are experiencing in detail, and we will reply as soon as possible.
| Country and Region | Application List |
|---|---|
| Global | Global Application List |
| Mainland China | Mainland China Application List |
2 - Enhancing CDN Access Speed with ECS
AdGuard Private supports the ECS feature, providing more precise resolution to optimize your network experience.
Setup method: 
What is ECS (Extended Client Subnet)?
ECS (Extended Client Subnet) is a DNS protocol extension that allows the DNS resolver (such as your AdGuard Private server) to pass part of the client’s IP address information to the authoritative DNS server. This enables the authoritative server to provide more accurate DNS responses based on the client’s network location.
How ECS Works
Traditional DNS Query: Without ECS, the DNS resolver only sends its own IP address to the authoritative DNS server. This means the authoritative server can only make resolution decisions based on the location of the resolver (usually a data center), which may lead to suboptimal results.
DNS Query with ECS Enabled: When ECS is enabled, the DNS resolver includes a part of the client’s IP address (subnet) in the DNS query. For example, if the client’s IP address is
203.0.113.45, the resolver might send203.0.113.0/24as ECS information.Response from the Authoritative Server: Upon receiving a query with ECS information, the authoritative DNS server can use this information to select the most suitable IP address for the client. This typically means choosing a server geographically closest to the client.
Advantages of ECS
- Faster Response Times: By directing the client to the nearest server, ECS can reduce latency and improve application response times.
- Improved User Experience: Faster response times can lead to a smoother and more enjoyable online experience.
- More Efficient CDN Usage: Content Delivery Networks (CDNs) can use ECS to direct users to the optimal content server, thereby increasing efficiency and reducing costs.
- Bypassing Local Resolver Limitations: Some local network operators’ DNS servers may have issues, such as incorrect resolution or domain hijacking. Using ECS can bypass these limitations and obtain more accurate resolution results.
Why Use ECS in AdGuard Private?
AdGuard Private, as a private DNS server, can be configured to use upstream DNS servers for domain resolution. When ECS is enabled, AdGuard Private can pass your client subnet information to the upstream server, thereby obtaining more accurate resolution results.
3 - DDNS Dynamic Resolution
What is DDNS?
DDNS (Dynamic DNS) allows you to bind a fixed domain name to a dynamic IP address, suitable for home broadband users to access internal network devices such as NAS, smart home controllers, etc.
Features
- Easy to Use: Only one script is needed for automatic updates
- No Additional Cost: No need to purchase a domain name
- High Reliability: Relies on Adguard Private’s DNS infrastructure
- Quick Effect: DNS records take effect immediately after update, no need to wait for DNS propagation
Preparation for Use
To use the DDNS feature, you need:
- A valid Adguard Private service
- Username and password for the management panel
- The domain name to be resolved (e.g., nas.home)
DDNS script download:
Configuration Steps
1. Gather Necessary Information
You need to prepare:
- Adguard Private service address, like:
https://xxxxxxxx.adguardprivate.com - Administrator username and password
- The domain name to be resolved, like:
nas.home
2. Deploy the Update Script
The following script will automatically update the resolution address of the specified domain.
Windows PowerShell
# Download the script
Invoke-WebRequest -Uri https://www.adguardprivate.com/docs/startup/private/tutorial/ddns/update_dns.ps1 -OutFile update_dns.ps1
# Set execution policy (optional, only for the current session)
Set-ExecutionPolicy -ExecutionPolicy Unrestricted -Scope Process
# Execute the script
.\update_dns.ps1 https://xxxxxxxx.adguardprivate.com admin:password123 nas.home
Linux && MacOS
# Download the script
wget https://www.adguardprivate.com/docs/startup/private/tutorial/ddns/update_dns.sh -O update_dns.sh
# Add execution permission
chmod +x update_dns.sh
# Execute the script
./update_dns.sh https://xxxxxxxx.adguardprivate.com admin:password123 nas.home
Frequently Asked Questions
How to Verify if it’s Effective?
You can check if the resolution correctly points to your current IP address using the ping your-domain.name command.
Or log into the service backend and check the Filter -> DNS Rewrite records.
How to Set Up Scheduled Updates?
Windows Scheduled Task
- Open Task Scheduler
- Create a basic task
- Set the run frequency (recommended 15-30 minutes)
- Choose PowerShell as the program location, and enter the full command of the script as the argument
Linux Cron Task
Add the following to crontab (execute every 15 minutes):
*/15 * * * * /path/to/update_dns.sh https://xxxxxxxx.adguardprivate.com admin:password123 nas.home
Precautions
- Please keep your username and password safe to avoid leaks
- It is recommended to add the update script to the system’s scheduled tasks for automatic execution
- If the resolution does not take effect promptly, please check the network connection and the validity of the credentials
4 - DNS Split Configuration Guide
DNS Split Overview
DNS split can significantly enhance the network access experience by distributing resolution requests for different domain names to different DNS servers. A reasonable DNS split configuration can:
- Speed up domain name resolution
- Improve website access stability
- Optimize cross-border access experience
- Avoid DNS pollution issues
Adguard Private Split Configuration
Basic Configuration Example
# Domestic DNS server
223.5.5.5 # Ali DNS
2400:3200::1 # Ali DNS IPv6
public0.adguardprivate.svc.cluster.local # Private DNS, mainland upstream
# International DNS server
tls://1.0.0.1 # Cloudflare DNS
tls://[2606:4700:4700::1001] # Cloudflare DNS IPv6
public2.adguardprivate.svc.cluster.local # Private DNS, other upstream
# Split rule example
[/google.com/bing.com/github.com/stackoverflow.com/]tls://1.0.0.1 public2.adguardprivate.svc.cluster.local
[/cn/xhscdn.com/tencentclb.com/tencent-cloud.net/aliyun.com/alicdn.com/]223.5.5.5 2400:3200::1 public0.adguardprivate.svc.cluster.local
List of Domestic ISP DNS Servers
Telecom DNS Servers
| Name | Primary DNS Server | Secondary DNS Server |
|---|---|---|
| Anhui Telecom | 61.132.163.68 | 202.102.213.68 |
| Beijing Telecom | 219.142.76.3 | 219.141.140.10 |
| Chongqing Telecom | 61.128.192.68 | 61.128.128.68 |
| Fujian Telecom | 218.85.152.99 | 218.85.157.99 |
| Gansu Telecom | 202.100.64.68 | 61.178.0.93 |
| Guangdong Telecom | 202.96.128.86 | 202.96.128.166 |
| Guangxi Telecom | 202.103.225.68 | 202.103.224.68 |
| Guizhou Telecom | 202.98.192.67 | 202.98.198.167 |
| Henan Telecom | 222.88.88.88 | 222.85.85.85 |
| Heilongjiang Telecom | 219.147.198.230 | 219.147.198.242 |
| Hubei Telecom | 202.103.24.68 | 202.103.0.68 |
| Hunan Telecom | 222.246.129.80 | 59.51.78.211 |
| Jiangsu Telecom | 218.2.2.2 | 218.4.4.4 |
| Jiangxi Telecom | 202.101.224.69 | 202.101.226.68 |
| Inner Mongolia Telecom | 219.148.162.31 | 222.74.39.50 |
| Shandong Telecom | 219.146.1.66 | 219.147.1.66 |
| Shaanxi Telecom | 218.30.19.40 | 61.134.1.4 |
| Shanghai Telecom | 202.96.209.133 | 116.228.111.118 |
| Sichuan Telecom | 61.139.2.69 | 218.6.200.139 |
| Tianjin Telecom | 219.150.32.132 | 219.146.0.132 |
| Yunnan Telecom | 222.172.200.68 | 61.166.150.123 |
| Zhejiang Telecom | 202.101.172.35 | 61.153.177.196 |
| Tibet Telecom | 202.98.224.68 | 202.98.224.69 |
Unicom DNS Servers
| Name | Primary DNS Server | Secondary DNS Server |
|---|---|---|
| Beijing Unicom | 123.123.123.123 | 123.123.123.124 |
| Chongqing Unicom | 221.5.203.98 | 221.7.92.98 |
| Guangdong Unicom | 210.21.196.6 | 221.5.88.88 |
| Hebei Unicom | 202.99.160.68 | 202.99.166.4 |
| Henan Unicom | 202.102.224.68 | 202.102.227.68 |
| Heilongjiang Unicom | 202.97.224.69 | 202.97.224.68 |
| Jilin Unicom | 202.98.0.68 | 202.98.5.68 |
| Jiangsu Unicom | 221.6.4.66 | 221.6.4.67 |
| Inner Mongolia Unicom | 202.99.224.68 | 202.99.224.8 |
| Shandong Unicom | 202.102.128.68 | 202.102.152.3 |
| Shanxi Unicom | 202.99.192.66 | 202.99.192.68 |
| Shaanxi Unicom | 221.11.1.67 | 221.11.1.68 |
| Shanghai Unicom | 210.22.70.3 | 210.22.84.3 |
| Sichuan Unicom | 119.6.6.6 | 124.161.87.155 |
| Tianjin Unicom | 202.99.104.68 | 202.99.96.68 |
| Zhejiang Unicom | 221.12.1.227 | 221.12.33.227 |
| Liaoning Unicom | 202.96.69.38 | 202.96.64.68 |
National Mobile DNS IP
| Name | Primary DNS Server | Secondary DNS Server |
|---|---|---|
| Beijing Mobile | 221.130.33.60 | 221.130.33.52 |
| Guangdong Mobile | 211.136.192.6 | 211.139.136.68 |
| Jiangsu Mobile | 221.131.143.69 | 112.4.0.55 |
| Anhui Mobile | 211.138.180.2 | 211.138.180.3 |
| Shandong Mobile | 218.201.96.130 | 211.137.191.26 |
Public DNS IP
| Name | Primary DNS Server | Secondary DNS Server |
|---|---|---|
| 114 DNS | 114.114.114.114 | 114.114.115.115 |
| CNNIC SDNS | 1.2.4.8 | 210.2.4.8 |
| Aliyun Public DNS | 223.5.5.5 | 223.6.6.6 |
| DNSPod DNS+ | 119.29.29.29 | 119.29.29.29 |
| Google DNS | 8.8.8.8 | 8.8.4.4 |
Configuration Recommendations
- Prioritize nearby DNS servers
- Configure both IPv4 and IPv6 DNS
- Set up backup DNS for important domains
- Regularly update split rules
- Monitor DNS response time
Precautions
- Record original DNS settings before configuration
- Avoid using untrusted DNS servers
- Regularly check if DNS resolution is normal
- Keep the rule list concise and effective
By reasonably configuring DNS split, you can significantly enhance the network access experience. It is recommended to choose appropriate DNS servers and split rules based on actual needs.
References
5 - Using Custom Device Names
If you directly use the service’s listening address, such as:
tls://xxxxxxxx.adguardprivate.comhttps://xxxxxxxx.adguardprivate.com/dns-query
The IP shown in the Client Rankings in the backend will be the cluster IP of the load balancer, which is meaningless to users and does not distinguish between different devices.
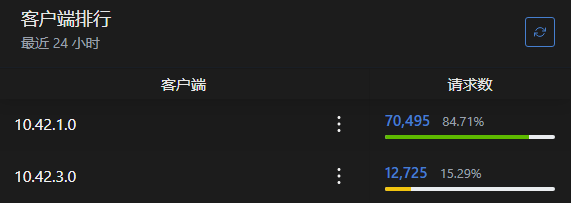
You can identify different devices by using extended domain names and adding URL paths.
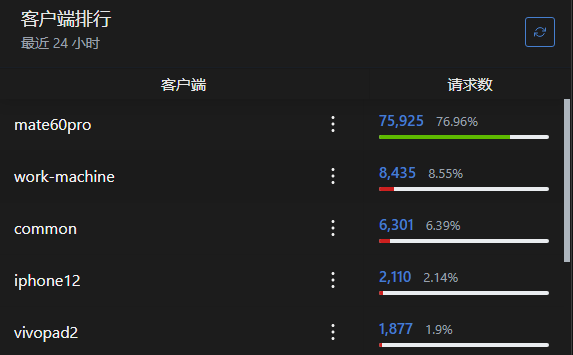
- DoT uses the extended domain name method, such as
tls://device1.xxxxxxxx.adguardprivate.com - DoH uses the method of adding a URL path, such as
https://xxxxxxxx.adguardprivate.com/dns-query/device2
Note:
- When setting up on Android devices, you do not need to enter the protocol prefix
tls://, just enterdevice1.xxxxxxxx.adguardprivate.com - For Apple devices, enter the client ID in the setup guide, download the configuration file to set up, no manual input is required
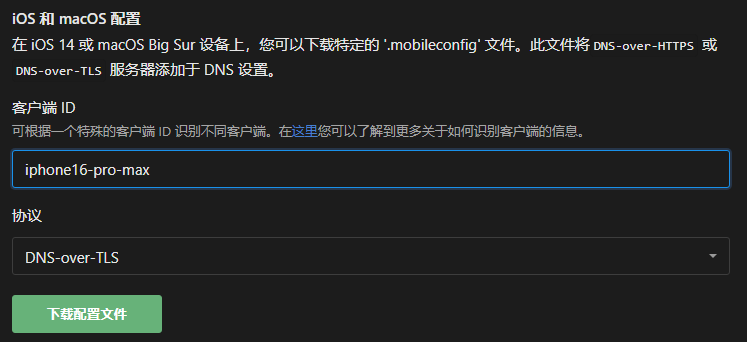
All devices of a personal service share the service’s query limit of
30requests per second.
6 - Faster Request Response
Paid users using AdGuard’s private service have the following DNS request path:
Based on the path, the fastest response scheme can be analyzed.
Local Cache Hit
The fastest response is a local cache hit. Since the local cache is at the memory level, it is very fast, taking only a few microseconds.
This is controlled by the TTL (time to live) value of the DNS response, typically ranging from a few minutes to several hours, indicating that the query result is valid during this time and does not need to be queried again.
You can set the minimum TTL value in Control Panel -> Settings -> DNS Settings -> DNS Cache Configuration -> Override Minimum TTL Value. Increasing this value extends the cache time, allowing the system to use the local cache more often. The typical TTL value is 600 seconds.
However, since this site also has filtering capabilities, if the service you need is mistakenly blocked by ad rules, you won’t be able to access it immediately even if you temporarily disable encrypted DNS, because the local cache result has been modified by the filtering rules. Therefore, setting it to 60 seconds is a safer value, ensuring that in rare cases, users won’t have to wait too long after disabling encrypted DNS due to misblocking.
AdGuard DNS Server
Currently, this site uses Alibaba Cloud servers located in Hangzhou, which can meet the low-latency needs of most users in the eastern region. As the business grows, servers will be added across the country in the future.
Server Cache Hit
By default, 4MB of DNS cache is set for each user, which is sufficient for a household based on experience. Freely modifying this setting may lead to forced termination of user services, and this site has blocked the modification entry for this setting.
Upstream DNS Server
Due to the use of Alibaba Cloud services, the upstream DNS service also uses Alibaba Cloud’s DNS service, which is very fast, typically returning results within a few milliseconds.
Users have three ways to request the upstream DNS server:
- Load Balancing: This site uses load balancing by default, automatically selecting the fastest server to return results.
- Parallel Requests: This site currently does not restrict the use of parallel requests.
- Fastest IP Address: This setting is currently meaningless, and this site has blocked the modification entry for this setting.
Here’s why the Fastest IP Address is meaningless: the fastest IP needs to be chosen by the device actually accessing the service. When the AdGuard service runs in Hangzhou and the user is in Beijing, AdGuard will think the IP address in Hangzhou is the fastest, but in reality, the user’s access to services in Beijing is the fastest. Choosing the Hangzhou IP address would actually increase latency. Therefore, this site has blocked the modification entry for this setting. This setting might be useful in a user’s home network but is meaningless in public services.
Many factors affect network experience, such as server bandwidth, network congestion, server load, and network quality. Choosing the fastest IP address does not guarantee the fastest response speed; latency is just one factor, not the only one. To prevent users from setting it incorrectly and causing a decline in service quality, this site has blocked the modification entry for this setting.
Rule Filtering
The most commonly used mode is the blacklist list, from which users can choose. The blacklist hit uses a hash algorithm, so regardless of the number of rules, the hit time is O(1), and users do not need to worry about the hit time being too long due to a large number of rules.
However, after rule calculation, they are stored in memory, with each user’s service memory usage limited to within 300MB, which can meet the needs of most users. If a user has too many rules, it may lead to insufficient memory, causing the service to restart repeatedly and resulting in service interruption.
This site has temporarily blocked the use of third-party rules to avoid users introducing too many rules. In the future, with better restriction methods, the use of third-party rules will be reopened.
Summary
To achieve faster request responses, users can:
- Appropriately increase the minimum TTL value to increase the local cache hit rate.
- Set an appropriate DNS cache size (pre-set value).
- Choose to create a service in the geographically closest city (awaiting business development).
- Choose load balancing for no overseas needs; choose parallel requests for overseas needs.
- Use a blacklist rule that suits you, avoiding introducing too many rules.
7 - Setting Up Trusted Service Providers
When creating a paid service, the default setting uses faster domestic upstream services, including Ali’s IPv4 and IPv6 as well as DoT services.
Some service providers may have issues with incorrect DNS resolution, directing some overseas websites to the wrong IP addresses, resulting in inaccessibility. A common symptom is a certificate error in the browser.
To avoid resolution errors, you can switch to an upstream service provider like Cloudflare. When using such services, ensure you are using the DoH or DoT protocol to prevent hijacking.
Additionally, you need to disable domestic upstream services, as they are closer and faster, and AdGuard will prioritize them.
To disable an upstream service, simply add a # before the corresponding service IP.
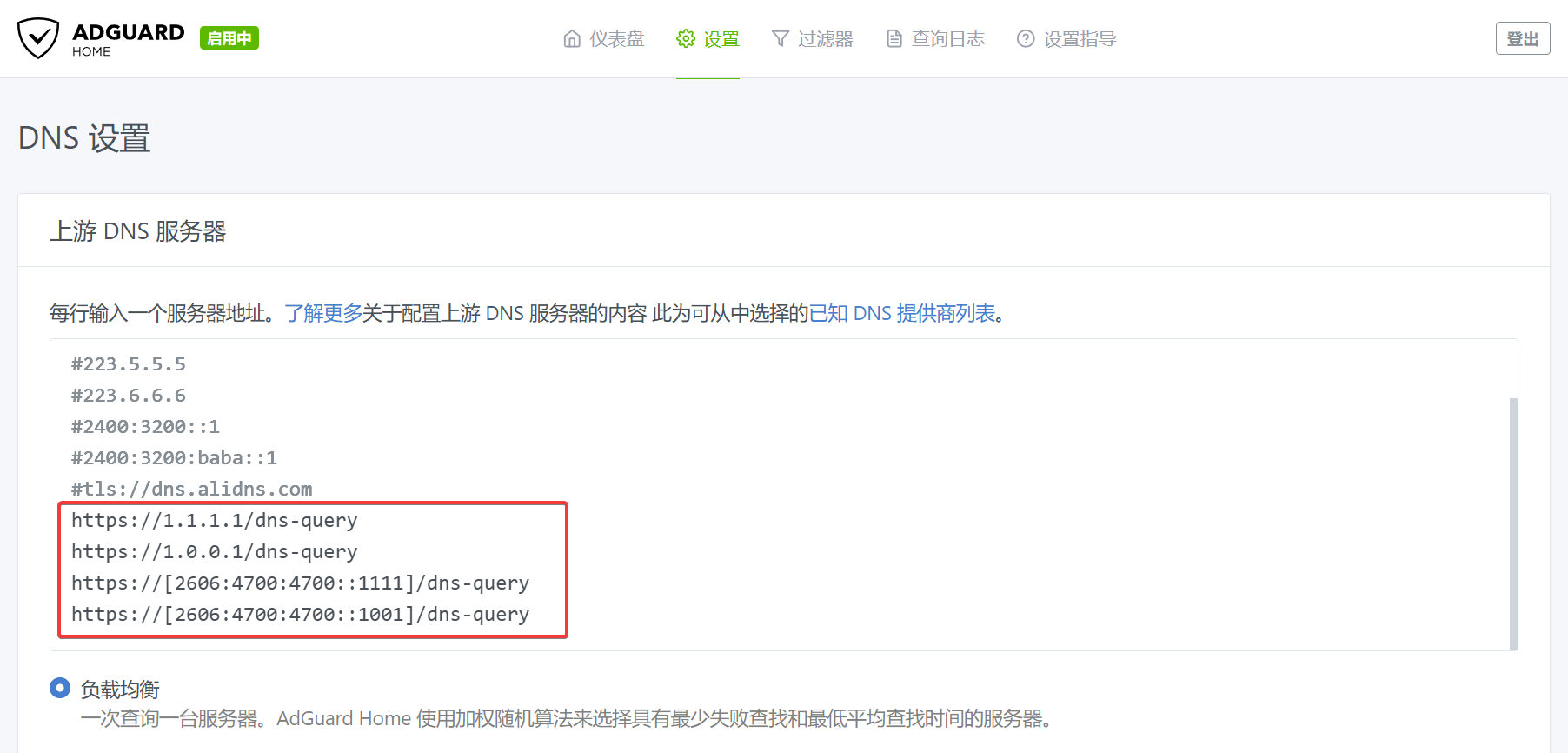
After setting up, you need to test the upstream to ensure the upstream server is available, and then apply the changes.
However, using only overseas services can degrade the access experience for domestic apps, as these apps typically route overseas resolutions to specific external servers, resulting in slower domestic access speeds.
If you only need to avoid resolution errors for commonly used services, you can manually specify a specific resolution address for the domains that are incorrectly resolved, while still using the default domestic upstream services for unspecified domains.
In the AdGuard console, go to Settings -> DNS Settings -> Upstream DNS Servers, and add the domains that are incorrectly resolved in the format [/example1.com/example2.com/]tls://1.0.0.1 to Custom DNS Servers, then click Save Settings.
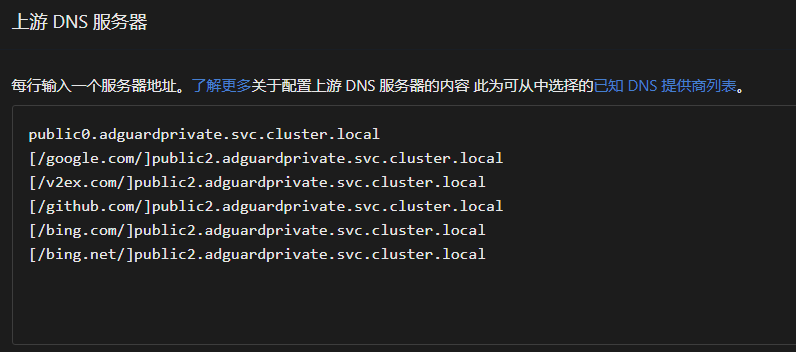
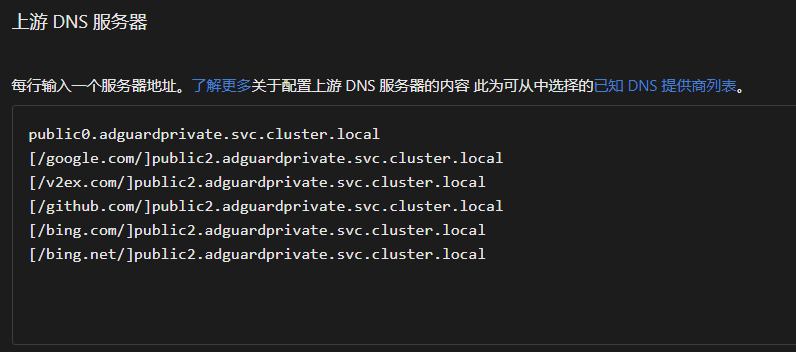
public2.adguardprivate.svc.cluster.local is our internally provided resolution service that avoids resolution errors, with the upstream set to Cloudflare. Compared to users manually specifying an overseas upstream, it offers faster resolution speeds, at the cost of a slight delay when updating domain resolutions. If you do not have specialized needs, you can use our provided resolution service that avoids errors.
If you need to use external resolution addresses from Cloudflare or Google, you must specify the IP using DoT/DoH. Here are some examples:
#tls://1.1.1.1
tls://1.0.0.1
tls://[2606:4700:4700::1111]
tls://[2606:4700:4700::1001]
tls://[2606:4700:4700::64]
tls://[2606:4700:4700::6400]
https://1.1.1.1/dns-query
https://1.0.0.1/dns-query
https://[2606:4700:4700::1111]/dns-query
https://[2606:4700:4700::1001]/dns-query
#tls://8.8.8.8
#tls://8.8.4.4
tls://[2001:4860:4860::8888]
tls://[2001:4860:4860::8844]
tls://[2001:4860:4860::64]
tls://[2001:4860:4860::6464]
#https://8.8.8.8/dns-query
#https://8.8.4.4/dns-query
#https://[2001:4860:4860::8888]/dns-query
https://[2001:4860:4860::8844]/dns-query
The addresses commented with
#are currently blocked by the firewall and temporarily unusable.
Our site fully supports IPv6, which is one of our advantages, allowing the use of IPv6 addresses for upstream services to achieve more stable resolution speeds.
